For security reasons, our Azure App Service has Access Restrictions configured to only allow traffic from specific IP Addresses. The problem is that these rules prevent us from being able to deploy our code through an Azure DevOps Hosted Agent CI/CD Pipeline. We set out to find a way to allow for this functionality in the safest, and most-automated fashion.
Microsoft does provide a list of the valid IP ranges for their hosted agents. However, the list changes frequently and would require significant effort (in my opinion) to automate this process and apply the whitelist on every App Service in our subscription.
Another option would have been to use a Private agent for our pipelines, that we could control and whitelist. This was our backup plan, but added another machine to manage.
The method we found to be the best fit for us, which I will detail here, was to use the release pipeline to get the IP address of the current hosted agent, dynamically whitelist it in the app service, deploy the code, then remove the whitelist entry. We initially tested this process by setting the rule to allow all (0.0.0.0/0) traffic while it was doing the deployment. That worked, but we wanted to try and get that to be more dialed-in. Here’s what we did:
- Azure DevOps Release Pipeline, running on a windows-2019 (latest) hosted agent
- Use an Azure CLI task (Powershell) to get the IP of the agent, and add the access restriction to the app service:
$myip = curl http://whatismyip.akamai.com/ | Select-Object -Expand Content
az webapp config access-restriction add --resource-group "<resourceGroup>" --name "<appService>" --rule-name "<ruleName>" --action Allow --ip-address $myip --priority 103

- Deploy the code to the App Service
- Run the OWASP ZAP Baseline Scan then transform and publish the test results.
Thanks to John Nunn's Blog for the assistance.
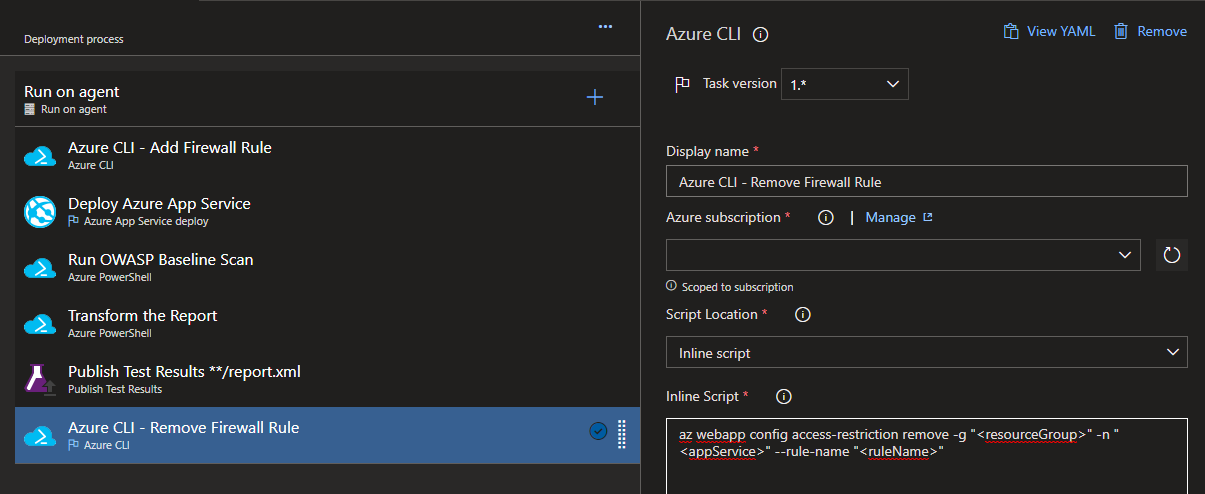
- Remove the IP whitelist:
az webapp config access-restriction remove -g "<resourceGroup>" -n "<appService>" --rule-name "<ruleName>"
|